If you need any help assessing your email security or investigating a BEC attack, do not hesitate to reach out to us.
Business Email Compromise (BEC) attacks are defined as the following by INTERPOL:
BEC fraud – also sometimes called CEO fraud – is a type of social engineering scam where criminals deceive company employees
into transferring money to them. They might gain access to the victim’s devices or systems through malware or other security
vulnerabilities, and learn enough about the company’s inner working to convincingly impersonate either a high-ranking employee
like the CEO or a supplier.
Many companies, especially SMEs are targeted by Business Email Compromise (BEC) attacks. They are very active, especially in the GCC, Europe and South America and often mostly from Nigeria. BEC scams accounted for half of cybercrime losses in 2019 and totaled $1.8Bn in 2019 - a 50% increase since 2018. For comparison, BEC associated losses were $1.3 billion in 2018, $676 million in 2017 and $360 million in 2016. Attackers usually start with phishing emails and can stay and monitor your emails for several months before starting to impersonate one of the account executives.
Last year, INTERPOL and the FBI carried severals arrests of key individuals. INTERPOL Investigators even reportedly found the details of more than 10,000 CEOs and financial accountants of companies on the suspect’s systems.
Although emails and phishing have been around of a long time, it is not always trivial to secure it and some solutions like Microsoft Office 365 make it particularly complex with a constantly changing user-interface and pseudo-hidden features (such as mail-forwarding and permission access) which are not scanned by their security products like Microsoft ATP and can be leveraged by attackers.
Although, Microsoft takes pride in the number of features they offer to customers they are definitely overwelhing and counter productive for SMEs that do not have a full time IT engineer. These downfalls make SMEs prime targets for BEC attackers.
Another downfall where financial institutions are failing, is that there is no effective way to shutdown bank accounts used by attackers since most of banks do not have easy way to reach out and report those accounts for investigations. Easiest would probably be to have a BEC Committee at the Federal/National levels where vicims can easily report information on cases to prevent more victims.
Last year, INTERPOL also launched a campaign called #BECareful.

Investigate
Azure Sign-Ins Logs
Get Sign-Ins Azure Active Directory logs of all the users in your organization to identify suspicious logins through the Azure Active Directory Portal.
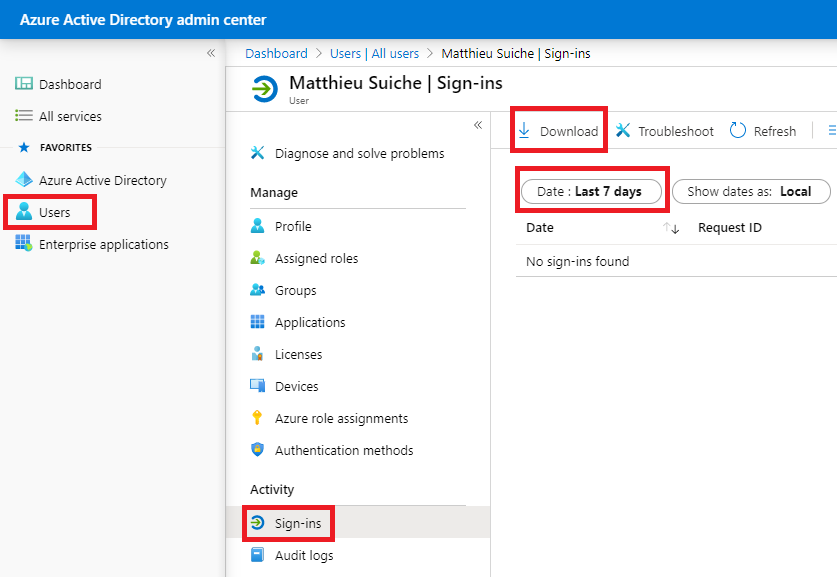
Those logs are exportable as a CSV file.
Message Trace
Retrieve the Message Trace of the suspected user accounts for all ingoing and outgoing emails. This way which of your customers has been contacted by the hackers from one of your mailbox and inform them ASAP, auto-forwarded emails (that may have been removed from the menu) but also to identify malicious emails received by one of the users. This can be done either through the Exchange Admin Center or through the Security & Compliance Center.
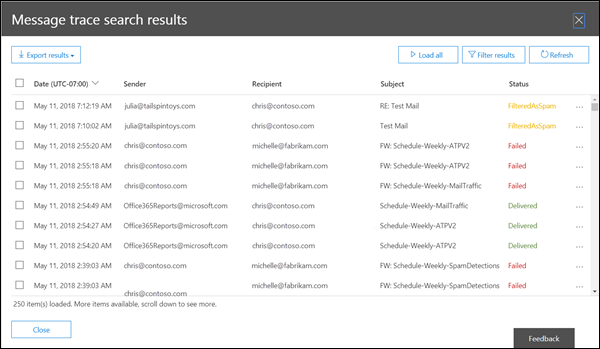
Those logs are exportable as a CSV file.
Mail-forwarding
Exchange Admin Center and Office 365 Admin Center are different, and both (!) can be used for email forwarding!
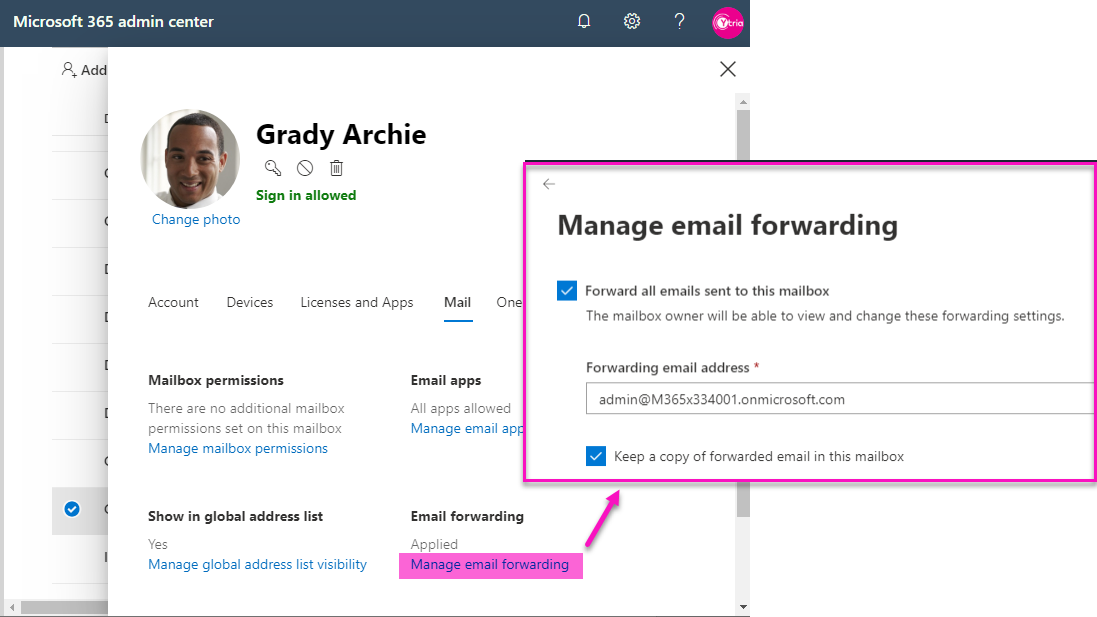
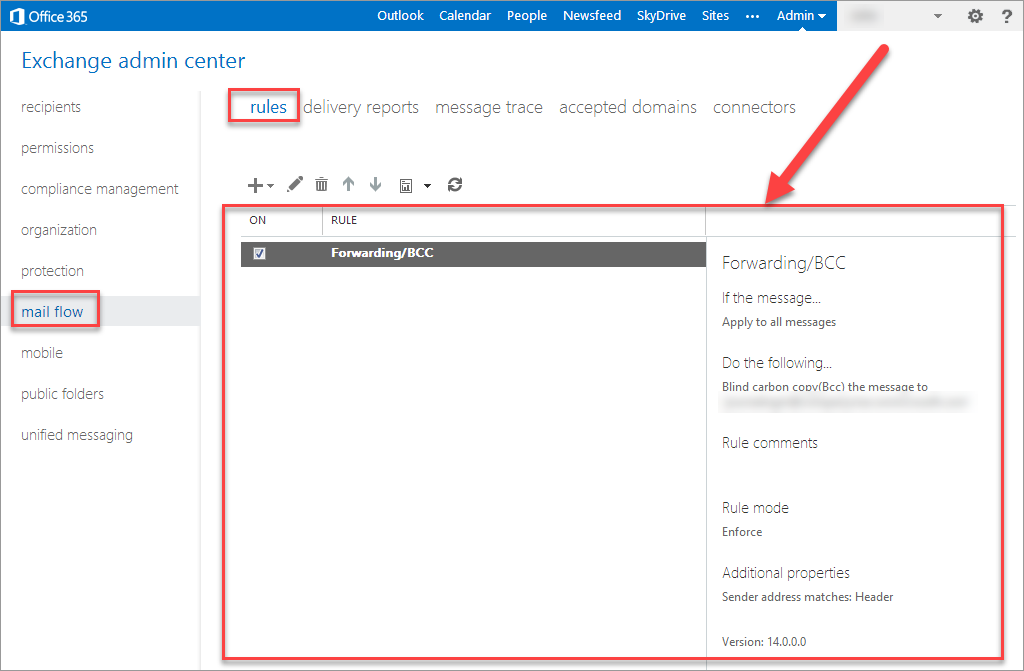
If an forwarding rule is set in O365, it won’t be visible in EAC. ¯_(ツ)_/¯
Permissions
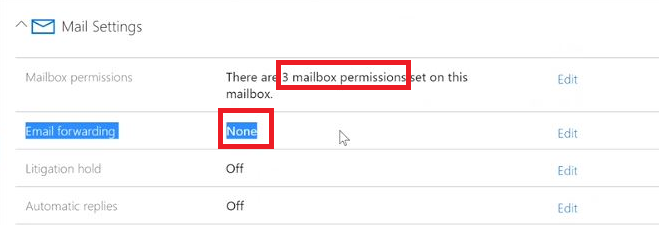
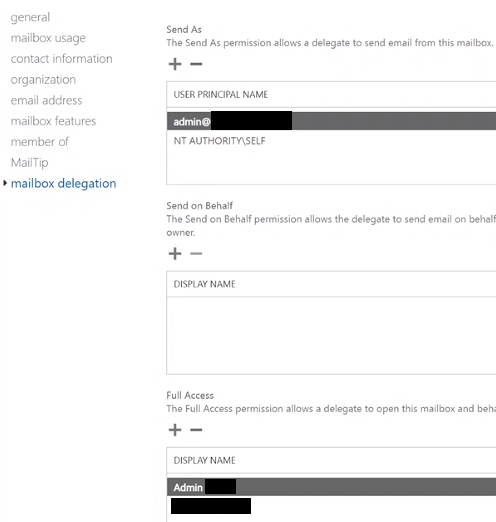
There is a feature, almost hidden, that allows to give mailbox permissions to another user via the Mailbox Delegation settings in O365. This can be used by an attacker to gain persistence after 2FA has been rolled out as no sign-ins activity will appear in the logs, and no 2FA errors will raise an alerts. Moreover, those permissions aren’t reviewed by Microsoft ATP.
Check the number of permissions under: Mail Settings > Mailbox Permissions.
Mitigate
Enable 2FA
Mandatory enforcement Two-Factor-Authentication (MFA/2FA/OTP) on all the employees’ Microsoft Office 365 accounts.
- Avoid using emails as a medium to receive MFA codes as they may also be forwarded if an account is compromised.
Phantom users
Check for unused accounts in your organization which may be soley used by the hacker. This is very important because if you roll out 2FA after an incident happen, the attacker may still have access to one unused mailbox and use this to gain persistence in the mailbox via Access Permissions to the CFO & CEO mailboxes.
Block autoforwarding
If a hacker gains access to a user’s mailbox, they can auto-forward the user’s email to an outside address and steal proprietary information. You can stop this by creating a mail flow rule.
Learn how to do that in this video.
Block phishing extensions
Microsoft 365 blocks potentially dangerous files, like JavaScript, batch, and executables, from being opened in Outlook. To increase this level of protection by adding rules that block or warn you of additional types of files. Learn how to do that in this video.
ATP Anti-Phishing
Phishing is a malicious attack where an email looks like it was sent from a familiar source, but it attempts to collect your personal information. By default, Microsoft 365 includes some anti-phishing protection, but you can increase that protection by refining the settings.
Upgrade to AAD P2 for users at risk
By default, you will only get 7 days of logs and very limited feature to investigate an incident. It is best to upgrade users at risk (CEO, CFO, Secretary) to AAD P2 to enable more control.
This will give you access to:
- named locations, to geographically restrict connections.
- 30 days of sign-in logs instead of 7 days.
Conclusion
There are so many layers that can be leveraged than attackers which we should not see any decrease in BEC attacks in 2020, and attackers are also expected to take advantage of the chaos created by the pandemic to conduct more successful BEC attacks.